A summary of all the protected health information (phi) your practice creates, receives or transmits. a list of every location, physical and digital, in protected health information in emr which your practice’s phi is stored. an assessment of your practice’s current security measures. an overview of possible threats/vulnerabilities in your practice’s protocols. “an ehr alters the mix of security needed to keep patient health information secure, and it brings new responsibilities for safeguarding your patients’ health information in an electronic form.
What Is Considered Protected Health Information Under Hipaa
Solution Solarity Medical Record Indexing Software
Hipaa’s data encryption standards allow health care providers, health insurance companies and business associates who transmit, store or access protected health information in electronic form to utilize a standardized level of data encryption when encryption is reasonable and appropriate. Mar 03, 2021 protected health information in emr · 5. 2. 3. 2 integration of emr with treatment planning systems 5. 2. 4 challenges 5. 2. 4. 1 integration between various oncology information systems within the healthcare industry. At a time when everybody is storing and transmitting personal information online, security is a high priority, and if your medical practice is one of many that uses electronic medical records (emr), protecting your patients' health information should be a top concern.
What Is Electronic Protected Health Information Ephi
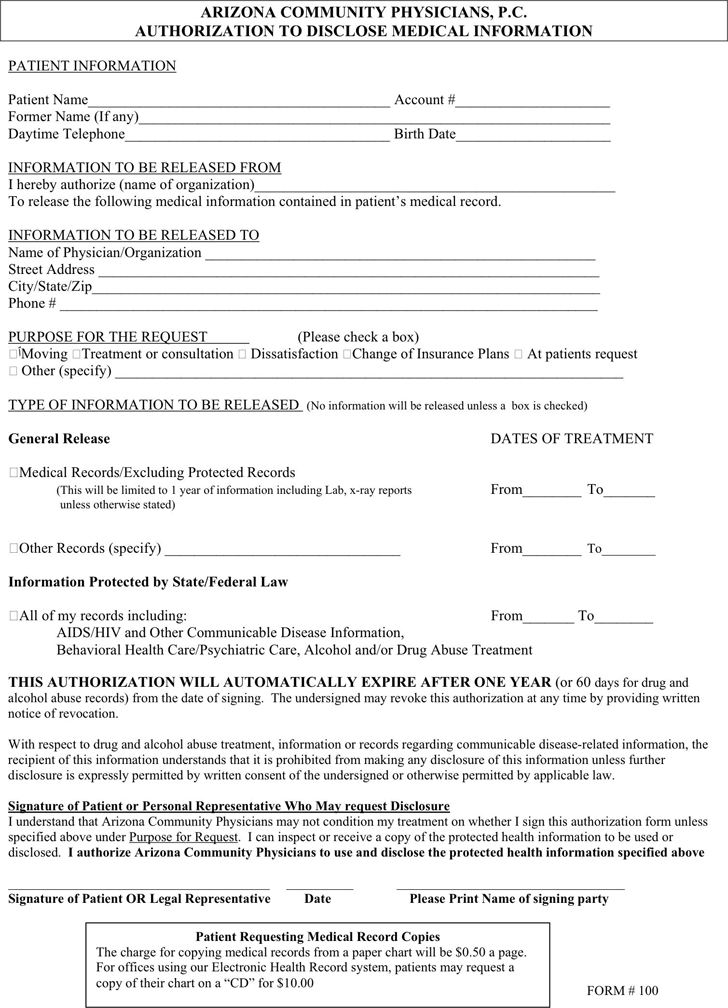
an individual's personal health information gave rise in 1996 to the creation health information (phi) were strengthened tremendously especially within While the terms ehr (electronic health records) and emr (electronic medical records) are often used interchangeably, they have slightly different meanings. the primary difference is that ehr puts forth the notion of interoperability, or interfacing with other medical systems to create a comprehensive view of a patient’s clinical information. Patient information security outlines the steps doctors must take to guard your "protected health information" (phi) from unauthorized access or breaches of privacy/confidentiality. security also refers to maintaining the integrity of electronic medical information. the emr must be continuously available, and system administrators must. Electronic protected health information (ephi) is protected health information (phi) protected health information in emr that is produced, saved, transferred or received in an electronic form. in the united states, ephi management is covered under the health insurance portability and accountability act of 1996 ( hipaa) security rule. in hipaa documentation, any organization or corporation that directly handles ephi is referred to as a covered entity.
Protectedhealthinformation is the term given to health data created, received, stored, or transmitted by hipaa-covered entities and their business associates in relation to the provision of healthcare, healthcare operations and payment for healthcare services. As of 2020, 393 protected health information breach incidents were reported to hhs in the past 12 months. they included malicious email hacking, unauthorized access to ehrs and medical records, as well as downloading phi on an unauthorized computer or device.
What Is Regarded As Protected Health Information According
desktops provide access to applications and data, including protected health information (phi), from any device, anywhere by securing the desktop experience in the cloud this type of availability is increasingly Electronic protected health information (ephi) is protected health information (phi) that is produced, saved, transferred or received in an electronic form. in the united states, ephi management is covered under the health insurance portability and accountability act of 1996 security rule. in hipaa documentation, any organization or corporation that directly handles ephi is referred to as a. Health care providers, other covered entities, and business associates may use mobile devices to access electronic protected health information (ephi) in a cloud as long as appropriate physical, administrative, and technical safeguards are in place to protect the confidentiality, integrity, and availability of the ephi on the mobile device and. Key information is automatically extracted from scanned documents & placed into the emr. access complete medical record. point of care scanning with solarity allows you to access 100% of the health record in the emr. automatically compare all discharges to the scanned charts.
However, so-called “super-confidential” information is protected by more stringent rules, which can complicate compliance efforts. super-confidential medical records containing drug and alcohol, mental health and hiv information are subject to more stringent federal and state laws under hipaa. Providing an updated way to keep medical records has made the health information technology market explode. converting and maintaining e-records is becoming easier every year. however, the long list of available emr system companies to choose from can be overwhelming and confusing. top emr systems list. Under hipaa, protected health information is considered to be individually identifiable information relating to the past, present, or future health status of an individual that is created, collected, or transmitted, or maintained by a hipaa-covered entity in relation to the provision of healthcare, payment for healthcare services, or use in.
Policies Procedures And References Uc Davis Health
Since ehr/emr data is considered patient health information, these kinds of records are under federal protection. the law that guards and preserves phi is hipaa the health insurance portability and accountability act. The proposed changes to the hipaa privacy rule include strengthening individuals’ rights to access their own health information, including electronic sharing of phi in an electronic health record (ehr) among covered health care providers and health.
Protectedhealthinformation is the term used to describe individually identifiable information associated with an individual’s healthcare. it may be created, stored or shared by a hipaa-covered entity while providing healthcare, or used in relation to payment for medical care services. under hipaa, the following information is regarded as. The office of the national coordinator for health information technology (onc), in coordination with the u. s. department of health and human services (hhs) office for civil rights (ocr), created the guide to help you integrate privacy and security into your practice. the guide covers a variety of topics highlighted below. Protected health information is defined in the code of federal regulations and applies to health records, but not education records which are covered by other federal regulations, and neither records held by a hipaa-covered entity related to its role as an employer. in the case of an employee-patient, protected health information does not include information held on the employee by a covered entity in its role as an employer, only in its role as a healthcare provider. The security rule calls this information “electronic protected health information” (e-phi). 3 the security rule does not apply to phi transmitted orally or in writing. general rules. the security rule requires covered entities to maintain reasonable and appropriate administrative, technical, and physical safeguards for protecting e-phi.
Top emr systems list best electronic medical records systems.
Ucd health p&p 2306: legal medical record content/core elements; ucd health p&p 2317: documentation of research patient status in the electronic medical record (emr) ucd health p&p 2410: allowable uses and disclosures for protected health information (phi) ucd health p&p 2446: tracking disclosures of protected health information (phi). Medicare and medicaid ehr incentive programs. eligible professionals must conduct or review a security risk analysis for each ehr reporting period to ensure the privacy and security of their patients’ protected health information: modified stage 2 meaningful use requirement: protect patient health information objective measure. An electronic medical record (emr) is a digital version of the traditional paper-based medical record for an individual. protected health information (phi), also.
Covers protected health information (phi) in any medium, while the hipaa security rule covers electronic protected health information (e-phi). hipaa rules have detailed requirements regarding both privacy and security. your practice, not your electronic health record (ehr) vendor, is responsible for taking the steps needed to comply. Mar 31, 2020 · since our emr software is web-based, there’s no need to purchase or maintain expensive servers or security equipment; all data is encrypted, backed up and protected by the same technologies used by major financial institutions. so even if your pc crashes, all of your practice data is still safe and secure.
Summary of the hipaa security rule hhs. gov.